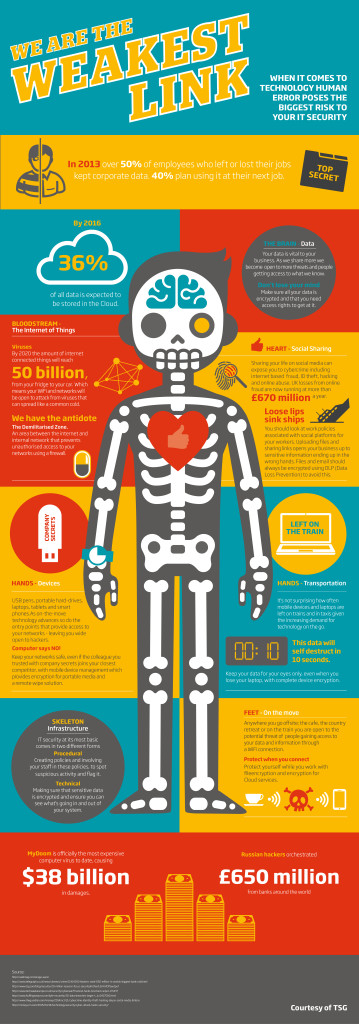
Did you know that there are more than 200,000 pieces of malicious code generated every day? If you own a business, you may not have considered how criminals can be targeting businesses both large and small. You need to ensure that your data is protected, so that your business remains safe and you don’t end up with a data leak. Hackers are no longer 15 year olds breaking into university websites and sites like Amazon, Ebay and CNN, and instead are professionals who collect data for financial gain, making them a huge danger to your business. In 2014 approximately one billion records were breached. And it’s getting worse every year. While it can be hard to know the answer to this huge problem, it’s evident that burying our head in the sand is not it.
Among the massive breaches were Home Depot (56 million records), Viator (1.4 million) and JPMorgan Chase at 83 million. The most famous? The Sony Pictures breach, which was apparently in response to the film The Interview” and no one truly reacted until the film was temporarily pulled from theatres. Apparently North Korea was to blame, and the fact is, in the current global climate, these breaches are often from hackers around the world. The fact that information travels so freely can also be a problem. When employees are traveling with mobile phones, USBs etc, they should always be encrypted in the off chance that they are lost or stolen. In fact employee theft is a big one, considering that 50% of employees who lost their jobs or left kept data in 2013. With 40% planning to use it at their next job, this is a huge leak that could easily be plugged with mobile device management. This is an encryption for portable media, and best of all, it comes with a remote wipe solution- meaning that disgruntled employee can’t take your data to your competition. Keep in mind that 36% of all data may be stored in the Cloud by 2016. That’s more than a third of the world’s data. As more and more things become connected to wifi (even things like our fridges, lights, cars, and other appliances), the wifi networks could be open to attack from viruses which would be easily spread and could cause untold damage. Imagine what the ability to shut down someone’s power could do if in the wrong hands?
The answer? A Demilitarised zone. This is an area between your internal network and the internet which prevents unauthorised people from gaining access to your networks by using a firewall. Since so many people are constantly on the go, and continually connecting to public wifi hotspots, it’s no wonder they’re getting hacked by people who use these hotspots to gather your information. Luckily you can protect yourself in a few different ways, including cloud encryption and file encryption. For more information, check out the below infographic, or TSG’s recent blog post.